2017/10/14
Crypto
贝斯的一家
1UjFrelJFMVJXbGRIUlRORVQwNHlRMGRaTTBSTlVWcFVSMUV6UkU5T1MwZEhUVmxVUzFKU1ZVZEpXbFJKVGxwVVIxa3lWRXRTVWxkSVJWcFVSMDVMUjBkVk0wUkhUVnBZUjBrelZGTk9TMGRIVFRSVVRWSlNWMGxaTTBSSlRqSkY=
依次base64、base64、base32、base16解码。
flag{fl4g_1_B4se_i3_V3ry_9ood}
颜文字
1゚ω゚ノ= /`m´)ノ ~┻━┻ //*´∇`*/ ['_']; o=(゚ー゚) =_=3; c=(゚Θ゚) =(゚ー゚)-(゚ー゚); (゚Д゚) =(゚Θ゚)= (o^_^o)/ (o^_^o);(゚Д゚)={゚Θ゚: '_' ,゚ω゚ノ : ((゚ω゚ノ==3) +'_') [゚Θ゚] ,゚ー゚ノ :(゚ω゚ノ+ '_')[o^_^o -(゚Θ゚)] ,゚Д゚ノ:((゚ー゚==3) +'_')[゚ー゚] }; (゚Д゚) [゚Θ゚] =((゚ω゚ノ==3) +'_') [c^_^o];(゚Д゚) ['c'] = ((゚Д゚)+'_') [ (゚ー゚)+(゚ー゚)-(゚Θ゚) ];(゚Д゚) ['o'] = ((゚Д゚)+'_') [゚Θ゚];(゚o゚)=(゚Д゚) ['c']+(゚Д゚) ['o']+(゚ω゚ノ +'_')[゚Θ゚]+ ((゚ω゚ノ==3) +'_') [゚ー゚] + ((゚Д゚) +'_') [(゚ー゚)+(゚ー゚)]+ ((゚ー゚==3) +'_') [゚Θ゚]+((゚ー゚==3) +'_') [(゚ー゚) - (゚Θ゚)]+(゚Д゚) ['c']+((゚Д゚)+'_') [(゚ー゚)+(゚ー゚)]+ (゚Д゚) ['o']+((゚ー゚==3) +'_') [゚Θ゚];(゚Д゚) ['_'] =(o^_^o) [゚o゚][゚o゚];(゚ε゚)=((゚ー゚==3) +'_') [゚Θ゚]+ (゚Д゚) .゚Д゚ノ+((゚Д゚)+'_') [(゚ー゚) + (゚ー゚)]+((゚ー゚==3) +'_') [o^_^o -゚Θ゚]+((゚ー゚==3) +'_') [゚Θ゚]+ (゚ω゚ノ +'_') [゚Θ゚]; (゚ー゚)+=(゚Θ゚); (゚Д゚)[゚ε゚]='\\'; (゚Д゚).゚Θ゚ノ=(゚Д゚+ ゚ー゚)[o^_^o -(゚Θ゚)];(o゚ー゚o)=(゚ω゚ノ +'_')[c^_^o];(゚Д゚) [゚o゚]='\"';(゚Д゚) ['_'] ( (゚Д゚) ['_'] (゚ε゚+(゚Д゚)[゚o゚]+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚ー゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (o^_^o)+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (o^_^o)+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (c^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (c^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (c^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚ー゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (゚Θ゚)+ (゚Д゚)[゚o゚]) (゚Θ゚)) ('_');
aaencode ,在线解混淆 或在 chrome 的console里直接运行即可。其他还有jjencode,ppencode,rrencode等。
| |
你猜我像啥
1Li0tLS0gLi4tLS0gLi4uLi4gLS4uLi4tIC4uLi4uIC4tLS0tIC0uLi4uLSAtLS0tLiAuLi4uLiAt\nLi4uLi0gLi0tLS0gLS0tLS0gLi0tLS0gLS4uLi4tIC0tLS0uIC4uLi4uIC0uLi4uLSAuLi4uLSAt\nLS0uLiAtLi4uLi0gLS0tLS4gLi4uLi4gLS4uLi4tIC4tLS0tIC0tLS0tIC4tLS0tIC0uLi4uLSAu\nLS0tLSAuLS0tLSAtLS4uLiAtLi4uLi0gLi0tLS0gLi0tLS0gLS4uLi4gLS4uLi4tIC4tLS0tIC4u\nLS0tIC4tLS0tIC0uLi4uLSAuLS0tLSAtLS0tLSAtLS0uLiAtLi4uLi0gLi0tLS0gLi4tLS0gLS0t\nLS0gLS4uLi4tIC4tLS0tIC4tLS0tIC4uLi4tIC0uLi4uLSAuLS0tLSAuLS0tLSAtLS0tLSAtLi4u\nLi0gLi0tLS0gLS0tLS0gLi4uLi0gLS4uLi4tIC4tLS0tIC0tLS0tIC0tLS4uIC0uLi4uLSAuLi4u\nLiAuLS0tLSAtLi4uLi0gLi4uLi4gLi0tLS0gLS4uLi4tIC4tLS0tIC4uLS0tIC4uLi0tIC0uLi4u\nLSAuLS0tLSAuLS0tLSAtLS0tLSAtLi4uLi0gLi0tLS0gLi0tLS0gLi4uLi4=
| |
2017/10/23
WEB
WEB签到
签到,格式bdctf{xxxxx} http://2a8a372c90b9c52b54ac9f85234f6f20.yogeit.com:8080
| |
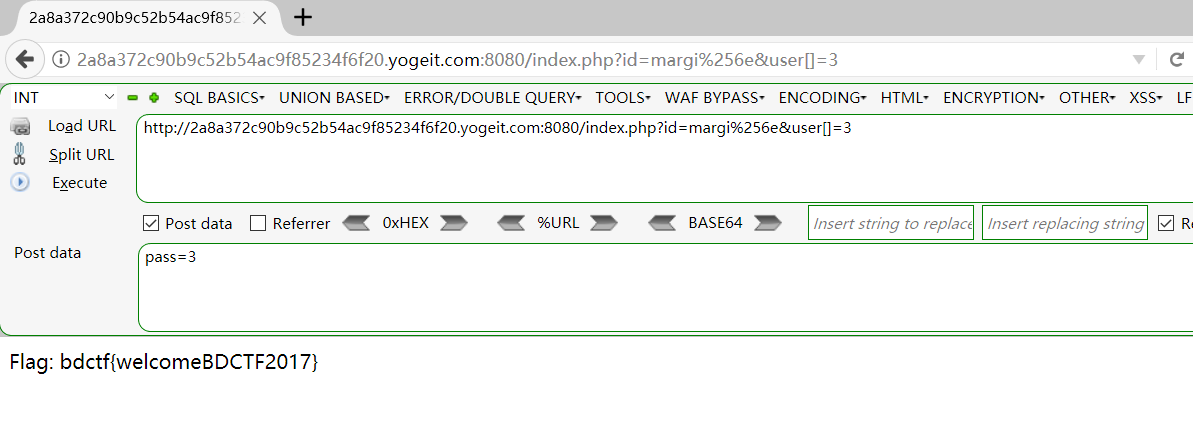
对数组进行哈希会返回null,所以传进去两个数组即可。Flag: bdctf{welcomeBDCTF2017}
命令注入
格式是flag{xxxx} http://c3f534c3e77ef68bda72e406337023fb.yogeit.com:8080
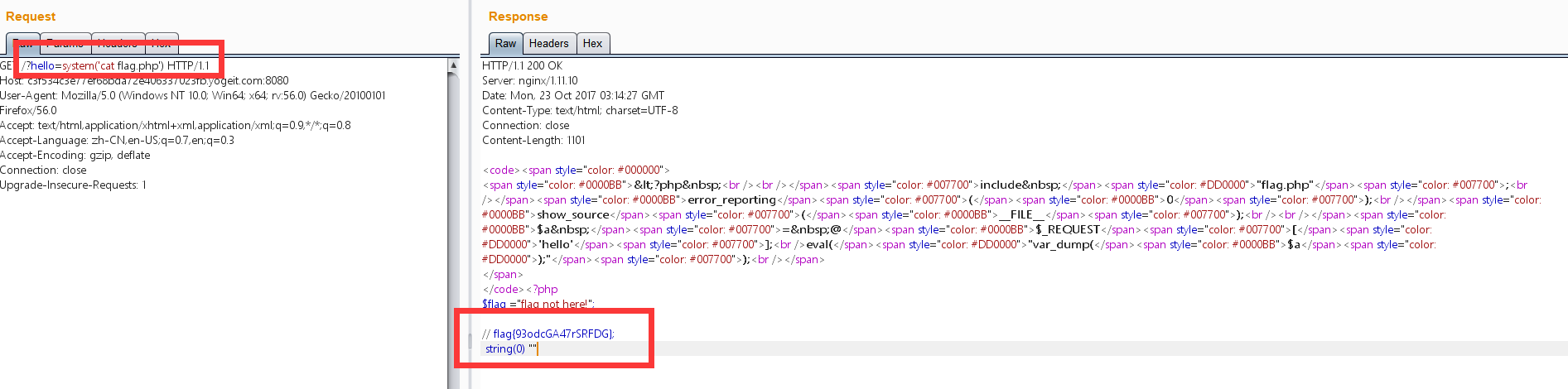
直接执行系统命令,system('cat flag.php') 。得到flag为flag{93odcGA47rSRFDG}
这不仅仅是WEB
格式bdctf{xxxxx} http://64fcfc546e0fafb5b4c327cc1eb36ec4.yogeit.com:8080
存在文件读取:
| |
访问不了惹。
MISC
MISC签到题
R1kzRE1RWldHRTNET04yQ0dZWkRHTVpXR0kzRElNWldHTVlUR01CVEdJWlRHTlJVR01ZVEdNUlRIRTNETU1aWkdZMlRHTVpUSEUzREVNWlVHWVlUR01SVEdZM0RFTVpaR000RE1NWlRHQTNETU1aVEdNM0RHTlJYSVE9PT09PT0=
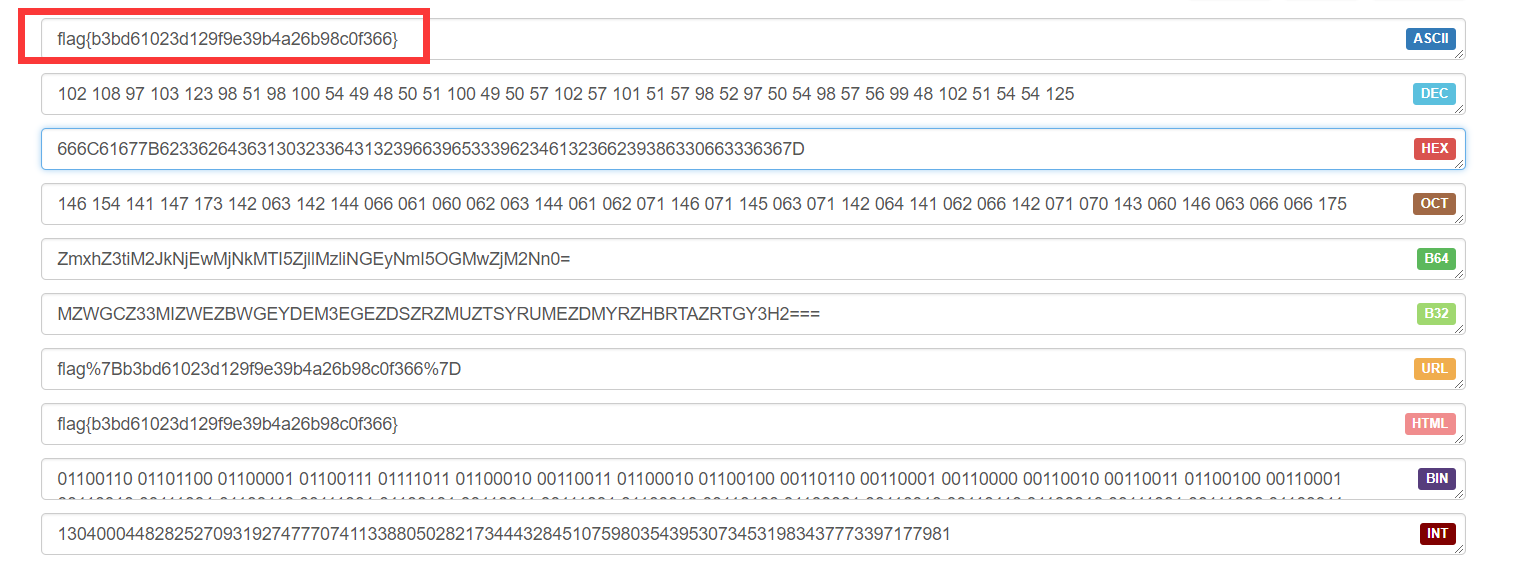
先base64解码,再base32解码,然后十六进制转ASCII码,得到flag为flag{b3bd61023d129f9e39b4a26b98c0f366}
常规杂项
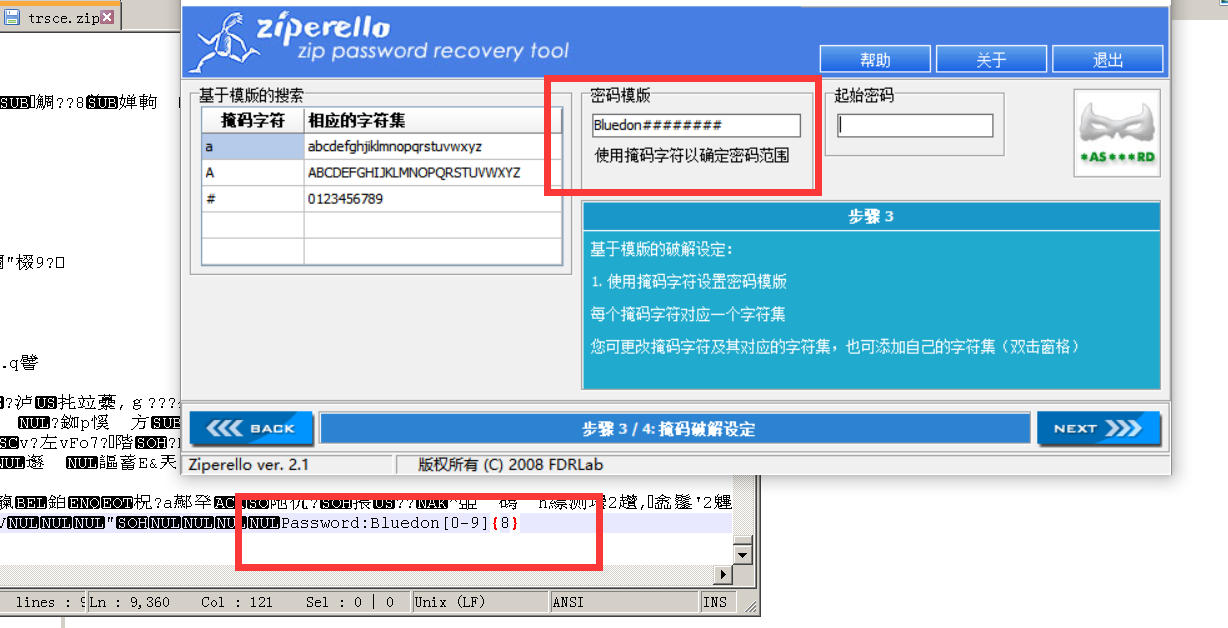
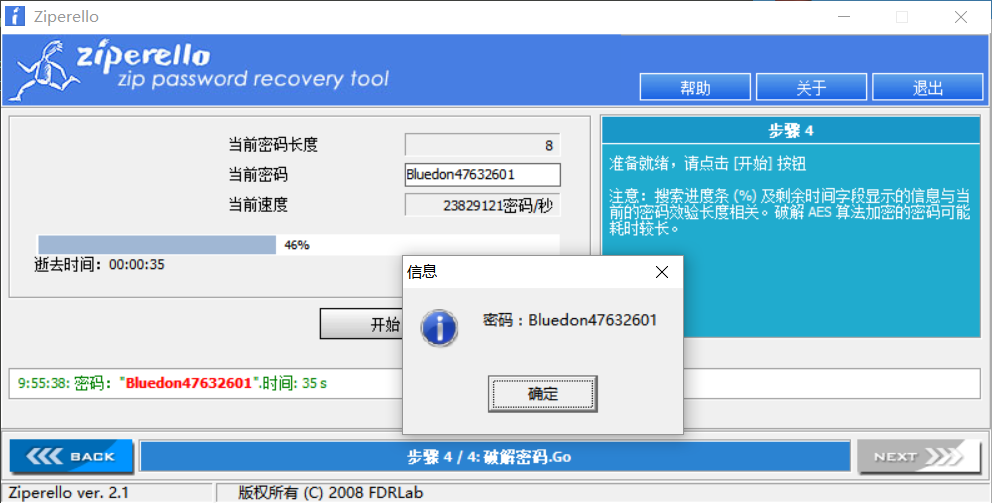
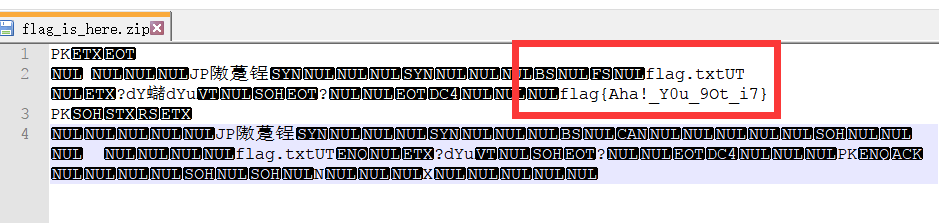
在文件末尾发现提示Password:Bluedon[0-9]{8} ,写python脚本生成字典,binwalk -e 提取出压缩包,使用ziperello爆破得到密码为Bluedon47632601,解压后还是一个压缩包,但应该是伪加密,用notepad++打开即可看到flag为flag{Aha!_Y0u_9Ot_i7}。
队友使用了ARCHPR掩码爆破,方便很多。
就在眼前
就在眼前 恩,如题。格式BDCTF{xxxxx}
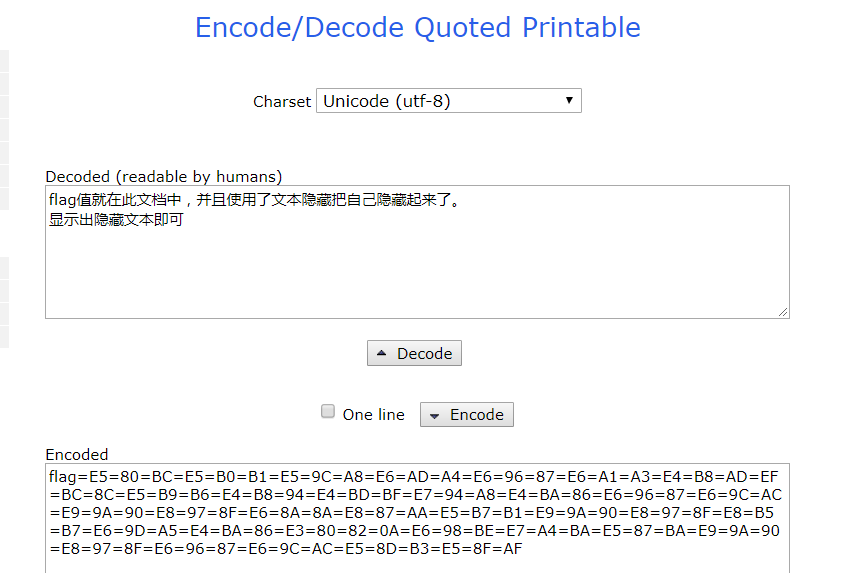
flag=E5=80=BC=E5=B0=B1=E5=9C=A8=E6=AD=A4=E6=96=87=E6=A1=A3=E4=B8=AD=EF=BC=8C=E5=B9=B6=E4=B8=94=E4=BD=BF=E7=94=A8=E4=BA=86=E6=96=87=E6=9C=AC=E9=9A=90=E8=97=8F=E6=8A=8A=E8=87=AA=E5=B7=B1=E9=9A=90=E8=97=8F=E8=B5=B7=E6=9D=A5=E4=BA=86=E3=80=82=0A=E6=98=BE=E7=A4=BA=E5=87=BA=E9=9A=90=E8=97=8F=E6=96=87=E6=9C=AC=E5=8D=B3=E5=8F=AF
使用了Quoted Printable encode,在线解码 可知隐藏了flag,让其显示即可。BDCTF{Y0u_4Re_5ucCe5SFul}
队友将文件另存为XML,打开也可见flag。

2017/10/30
web
签到题
更大的数,格式bdctf{xxx} http://1ccb637956167fe75634730d3d5e9d71.yogeit.com:8080
修改表单长度限制。bdctf{s0m2thing_ju8t_1ik2_thi8}
简单的题
格式flag{xxxx} http://f944ecfceaddb11ec591f23738496e52.yogeit.com:8080
post一个数组 password[]= 即可。flag{Y0u_4re_G3t_FLAG_452}
WEB100-2
提示是?hint,格式是flag{xxxx} http://78a06773a04246464d8eeadd2cdf28af.yogeit.com:8080
根据提示访问http://127.0.0.1/ctfoj/bdctf.php?hint 得到源码。
带上Cookie: BDCTF=s:21:"BDCTF:www.bluedon.com"%3b 即可得到flag{pBXeeZdOkG1QTP1} 。cookie中的分号要url编码一下。
蓝盾管理员
you are not bd-admin,格式bdctf{xxx} http://2a8da10821f39ea335a12fba77f7c3fc.yogeit.com:8080
访问view-source:http://2a8da10821f39ea335a12fba77f7c3fc.yogeit.com:8080/?file=php://filter/convert.base64-encode/resource=flag.php&user=php://input 同时post the user is bdadmin 得到bd-admin!<br>PD9waHAgIA0KLy9iZGN0ZntMZmlfQW5EX01vcmV9ICANCj8+ ,解码后得到bdctf{Lfi_AnD_More}
送大礼
格式bdctf{xxx} http://04c432a12784d2fb5ef431ec3366bc9a.yogeit.com:8080
访问 http://04c432a12784d2fb5ef431ec3366bc9a.yogeit.com:8080/flag.txt 有jsfuck,解开 后内容如下:
访问 http://04c432a12784d2fb5ef431ec3366bc9a.yogeit.com:8080/?bdctf=foo&flag=php://input 同时post foo 得到bdctf{UCCdlsZyVe} 。
火星撞地球
flag{1q2w3e4r} 密码就是答案,格式flag{xxxx} http://eef6f0186546043da56bf4c7f7e6d3ca.yogeit.com:8080
获取当前数据库名member
| |
当前数据库只有一个表
| |
当前表名为member
| |
当前表有四条记录
| |
得到列名’id,member_user,member_password,member_name,。。。'
| |
查询密码字段 burp爆破得到'5416d7cd6ef195a0f7622a9c56b55e84’,即'1q2w3e4r’。
| |
最后flag为flag{1q2w3e4r}
密室杀人案[x]
格式bdctf{xxxx} http://417c9d88ead6809efb1d310fe6832f56.yogeit.com:8080
| |
bluedon用户[x]
格式,bdctf{xxxxx} http://11537c131de3f8b2060b36c0cf7eb083.yogeit.com:8080
| |