题目:
- https://2018game.picoctf.com/problems
- 备用:https://findneo.github.io/p/picoCTF-2018-Problems.html
- 附件:https://github.com/findneo/ctfgodown/tree/master/20180929-picoctf
Forensics
Forensics Warmup 1
picoCTF{welcome_to_forensics}
Forensics Warmup 2
picoCTF{extensions_are_a_lie}
Desrouleaux
| |
Reading Between the Eyes
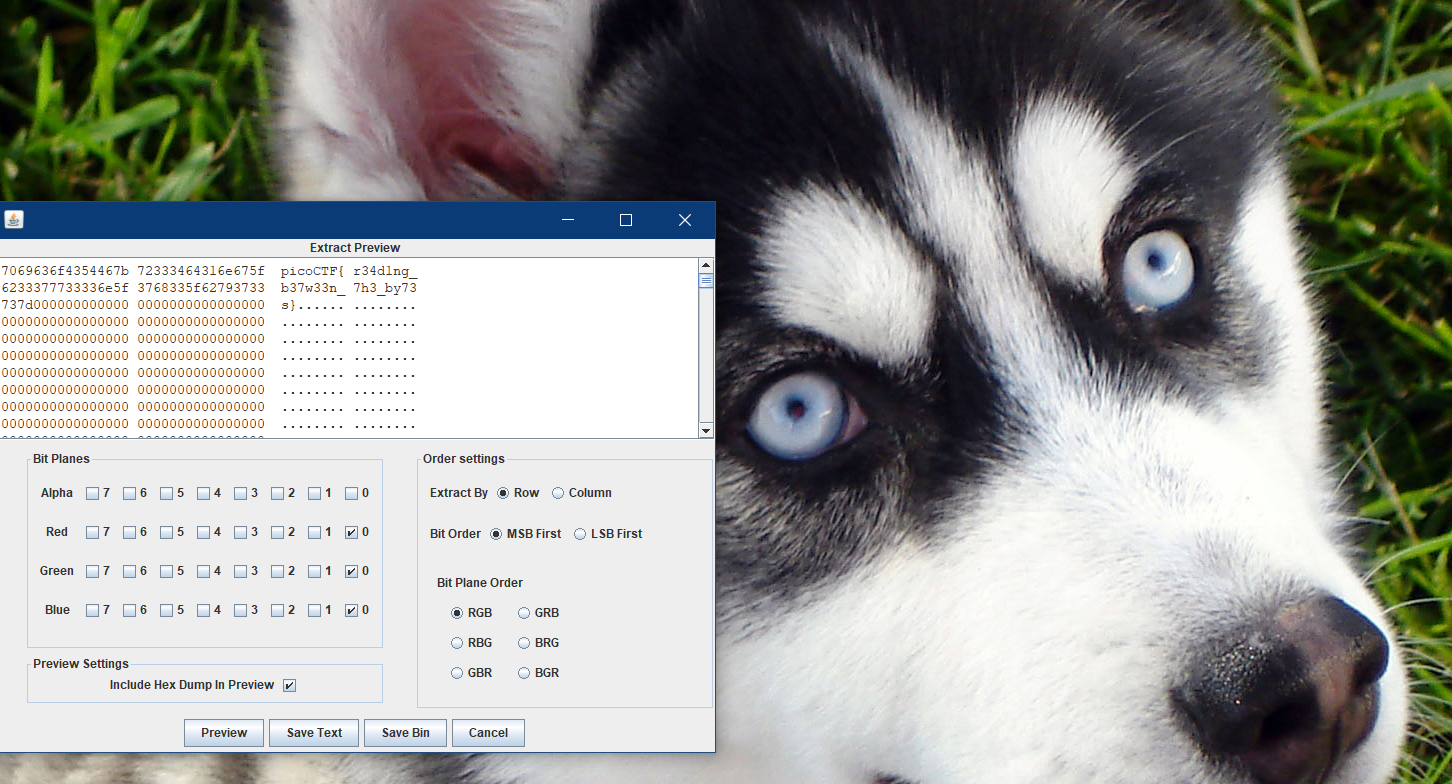
picoCTF{r34d1ng_b37w33n_7h3_by73s}
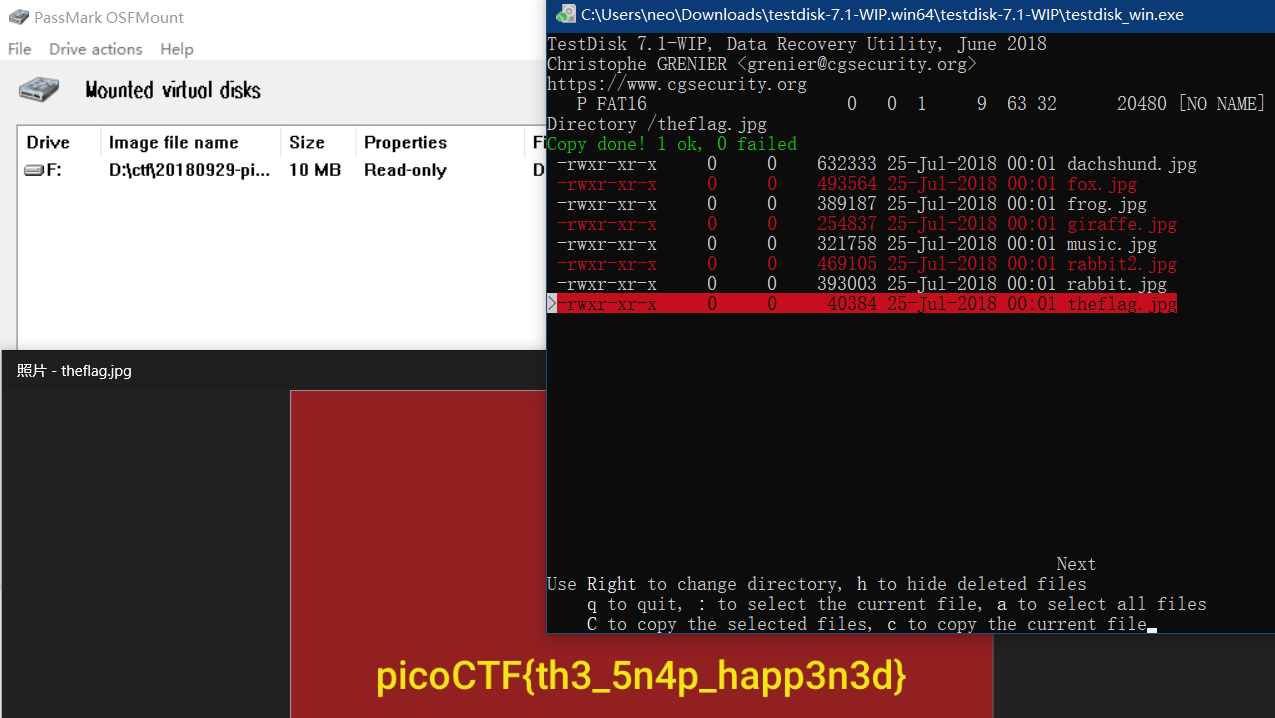
Recovering From the Snap
| |
参考 这里 ,使用OSFMount 挂载磁盘,使用 TestDisk & PhotoRec 7.1-WIP, Data Recovery 恢复被删除的theflag.jpg 。
picoCTF{th3_5n4p_happ3n3d}
admin panel
用wireshark打开,导出HTTP对象,其中一个文件内容是user=admin&password=picoCTF{n0ts3cur3_df598569} 。
hex editor
Truly an Artist
now you don’t
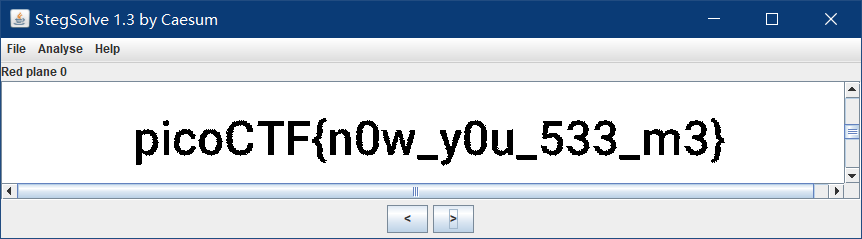
picoCTF{n0w_y0u_533_m3}
Ext Super Magic
根据提示使用debugfs查看img文件,发现幻数损坏。
从文档(https://wiki.osdev.org/Ext2#Superblock)可以看到使用ext2文件系统的第一步是寻找、提取、解析superblock。superblock总是从卷的1024字节开始,长度为1024字节。也就是说,如果一个扇区是512字节,那么superblock位于第2、3扇区。而在superblock中,ext2文件的signature(0xef53)位于第56、57两个字节,所以我们要修正文件的magic number为正确的signature,也就是修改(1024+56,1024+57)bytes即(1080,1081)bytes即(0x438,0x439)bytes的值为0xef53 。需注意采用小端序,低字节在低地址。
根据文档修改superblock,然后可以mount到系统,发现有个flag图片。
| |

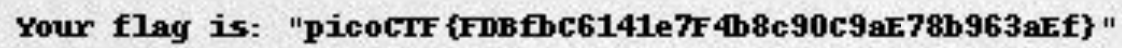
尝试了多个命令行OCR工具,tesseract-ocr效果最好,但识别结果还需要修正。
最后结果:picoCTF{FDBfbC6141e7F4b8c90C9aE78b963aEf}
Lying Out
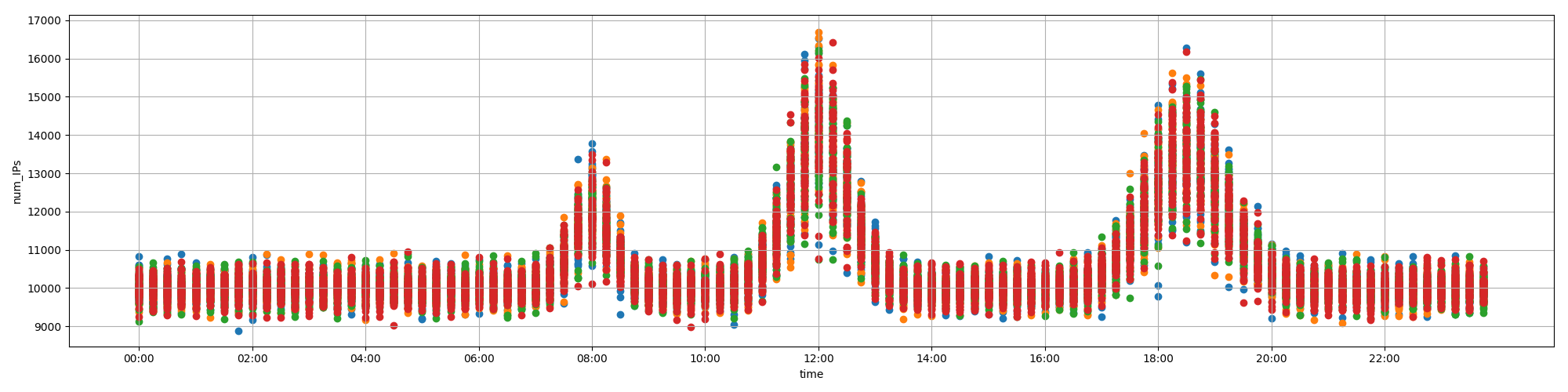
根据日常流量图判断流量可能异常的时间点。
| |
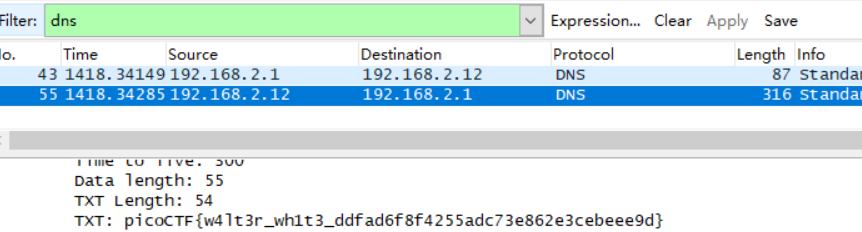
What’s My Name?
picoCTF{w4lt3r_wh1t3_ddfad6f8f4255adc73e862e3cebeee9d}
Malware Shops
附件貌似有问题,爆破出第一个答案是5,第二个随手交一下flag就出来了。
| |
LoadSomeBits
最低有效位隐写,需要fuzz起始偏移。
| |
core
core file或者core dunp是一个保存进程运行时内存镜像和进程状态(如寄存器的值等)的文件。没挂调试器的程序崩溃时一般会自动产生core文件用于post-mortem debugging。可以使用 gdb program [core dump] 开始调试。
| |
picoCTF{c96bd0fa2da5c0853cf12c4f93fce288}每个人的答案是不同的。
General Skills
absolutely relative
| |
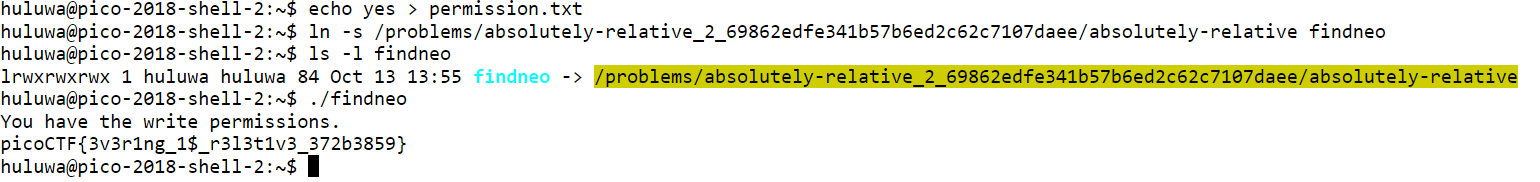
picoCTF{3v3r1ng_1$_r3l3t1v3_372b3859}
Aca-Shell-A
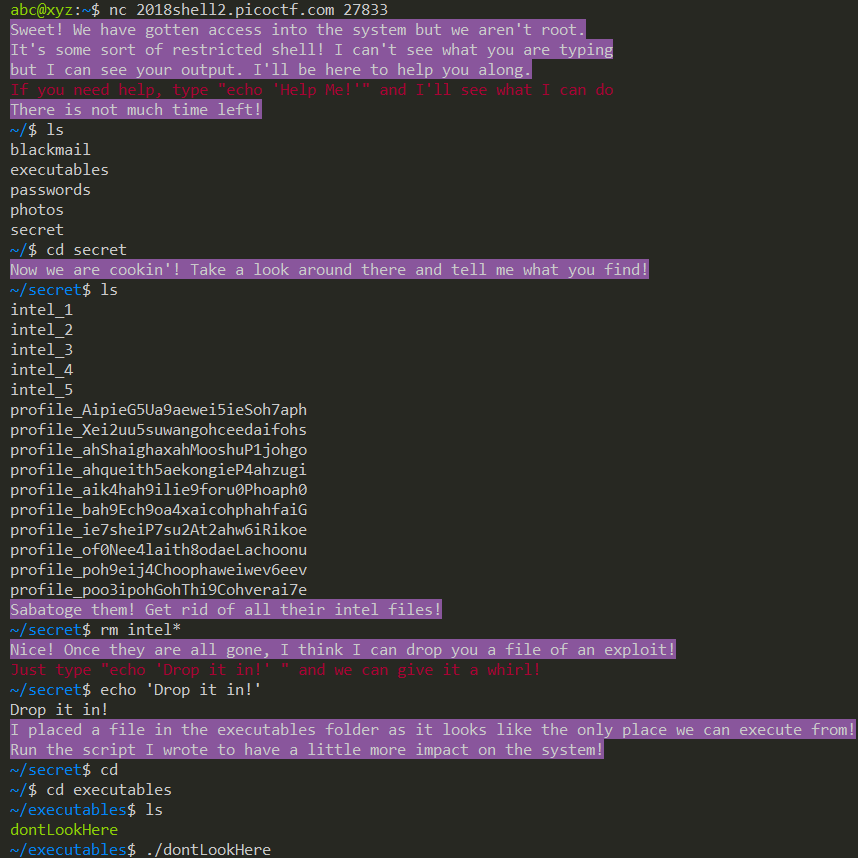
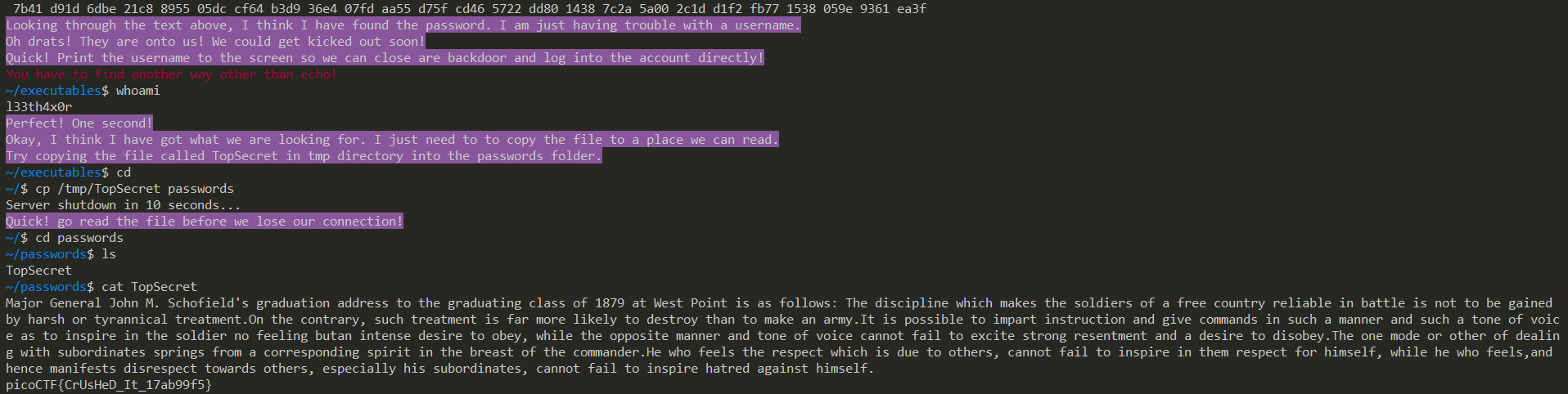
| |
in out error
learn gdb
picoCTF{gDb_iS_sUp3r_u53fuL_f3f39814}
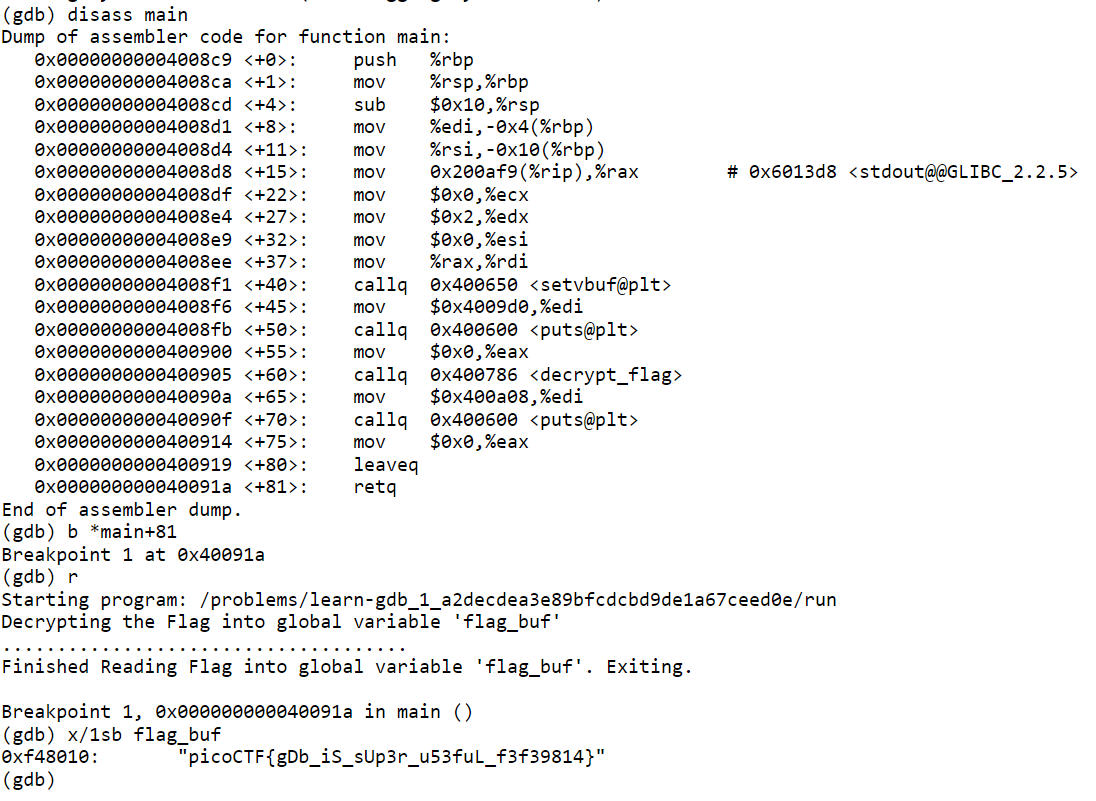
store
| |
整数溢出。
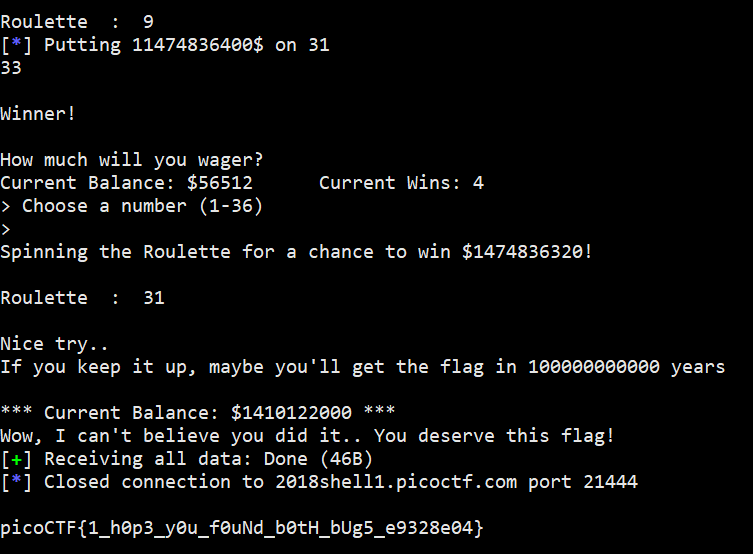
roulette
| |
提示说有两个bug。
其一出现在第27行,get_Long()函数的uint64_t l = 0; 。函数声明的返回值为long 型,实际返回值为uint64_t 型,前者有符号最大值为LONG_MAX:2^31-1 ,后者无符号最大值为ULONG_MAX:2^64-1 ,存在向上溢出为负数的风险。
真正使上溢成为可能的是32-35行 if(l >= LONG_MAX){l = LONG_MAX; break;} ,这个判断希望控制返回值不超过long 型数据的最大值,但应该写在while循环结束的地方而不是开始的地方,否则只能控制数据进入循环时符合条件,而离开时就不知道了,十倍以内都是可能的,而这足以溢出了。
到此为止,我们可以控制cash为任意值了,只要输入bet为 当前cash+2^32-目标cash ,在大概率(35/36)输的情况下,我们就能让cash变为想要的值。
要拿到flag还要求赢至少三次,那问题不大,下小注总会有赢的时候。按概率来算,总是对固定choice下注,可以期望在100次左右赢三次。但题目做了控制,太频繁交互会被禁止连接。于是看看其他的方法。
如果要改变wins,只能使choice与166行的 long spin = (rand() % ROULETTE_SIZE)+1; 相等,那么会发现这个随机数序列是在第52行播种的,种子就是我们的初始资金,是已知的。于是就可以知道每一次的spin了。EXP搬运自 https://github.com/sefi-roee/CTFs-Writeups/blob/master/picoCTF-2018/General/18-roulette-350/solution.md ,偷个懒就不写了。
picoCTF{1_h0p3_y0u_f0uNd_b0tH_bUg5_e9328e04}
| |
| |
scriptme
| |
solve.py
| |
picoCTF{5cr1pt1nG_l1k3_4_pRo_cde4078d}
binary exploitation
buffer overflow 0
picoCTF{ov3rfl0ws_ar3nt_that_bad_b49d36d2}
| |
Cryptography
Crypto Warmup 1
caesar cipher 2
hertz
替换密码。
在线工具:
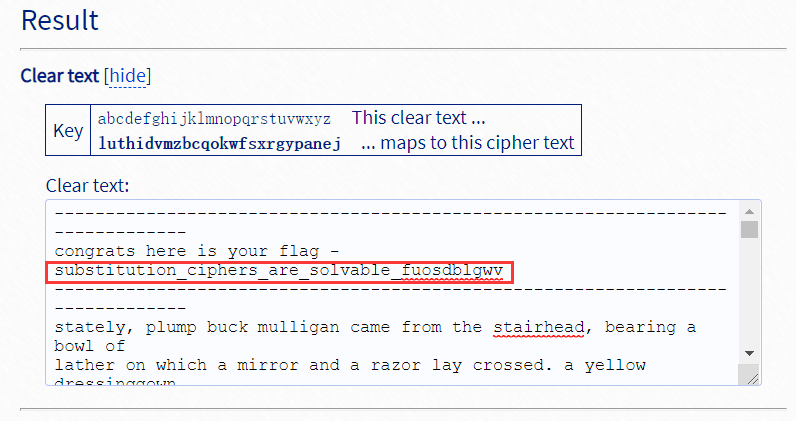
blaise’s cipher
在线解密即可:https://www.dcode.fr/vigenere-cipher 。逐步得到KEY长度为4,KEY为FLAG
picoCTF{v1gn3r3_c1ph3rs_ar3n7_bad_901e13a1}
Safe RSA
| |
【X】Super Safe RSA
参考RSA的广播攻击 。
| |
HEEEEEEERE’S Johnny!
| |
rsa-madlibs
回答一些简单的RSA知识。可以参考CTF中常见的RSA相关问题总结 一文。
发现一个做这类题目的好方法,python solve.py | nc 2018shell2.picoctf.com 18148 ,不到必要就不去处理各种奇怪的数据。
picoCTF{d0_u_kn0w_th3_w@y_2_RS@_b38be18a}
SpyFi
| |
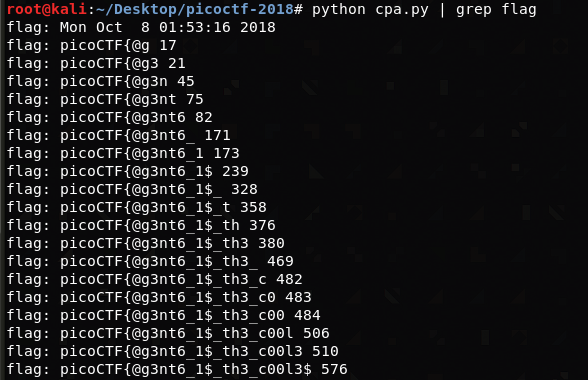
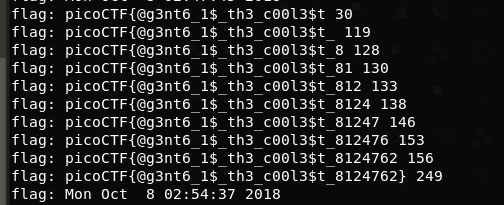
AES的ECB模式存在选择明文攻击。
当输入9个字节时,message中flag之外的部分长度为122个字节,密文长度为160个字节;当输入10个字节时,密文长度为176个字节。说明flag长度为160-122=38个字节。
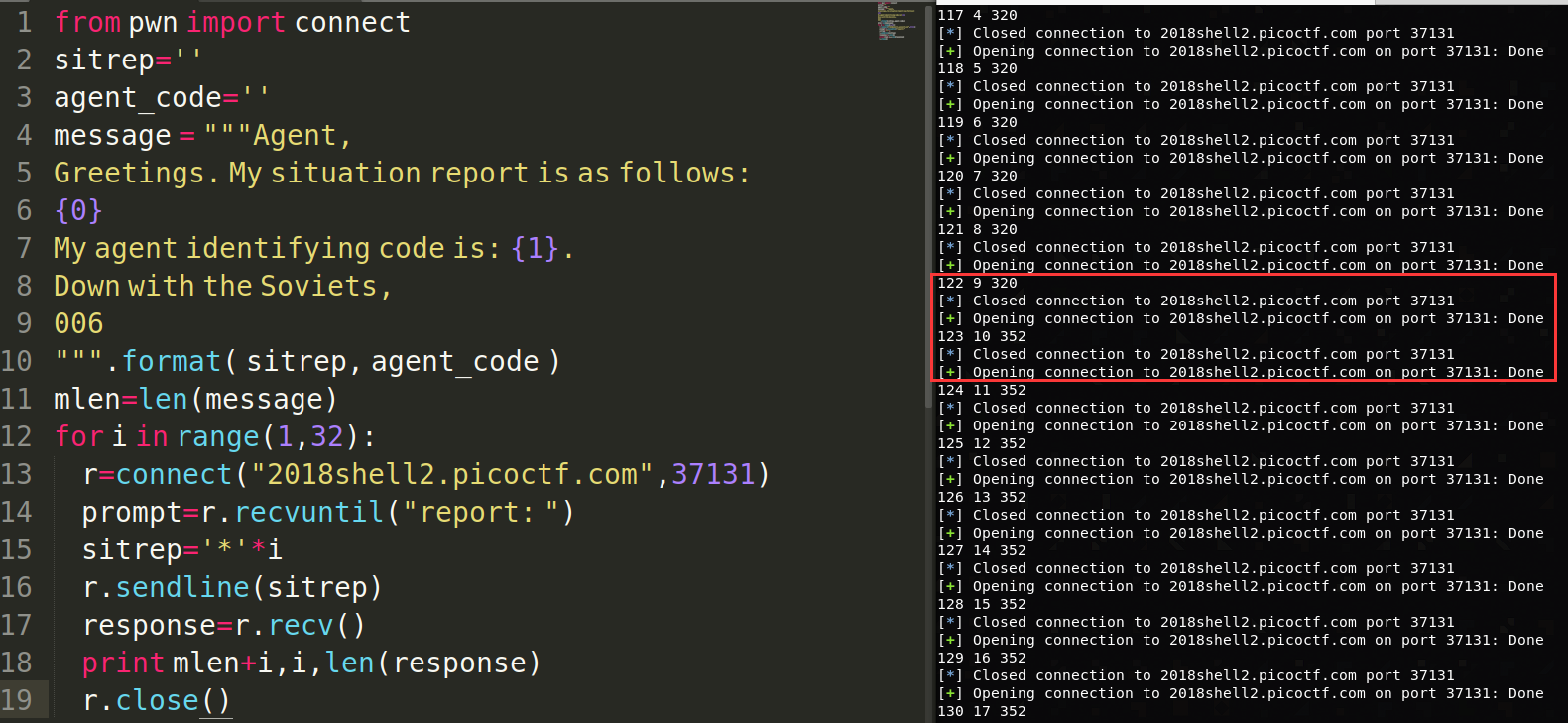
将message分组输出,看到爆破flag的机会。
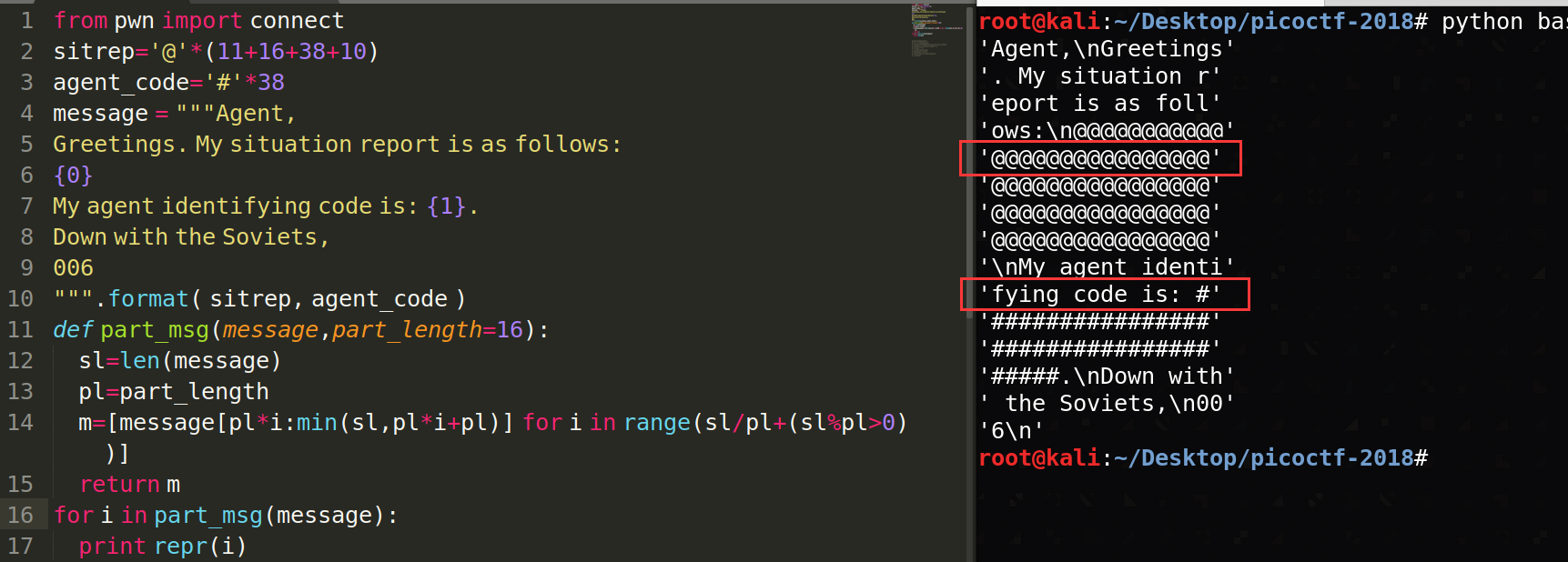
写完代码验证可行。

最后成果:
picoCTF{@g3nt6_1$_th3_c00l3$t_8124762}
全部代码:
| |
Web Exploitation
Buttons
Artisinal Handcrafted HTTP 3
先请求一下login页面:
发现表单是这样的:
| |
再请求登陆:
响应:
| |
带上cookie请求:
响应:
| |
【X】Secure Logon
| |
【X】A Simple Question
| |
reversing
assembly-0
What does asm0(0xd8,0x7a) return? 0x7a。
assembly-1
What does asm1(0xcd) return? 0xca。
| |
assembly-2
What does asm2(0x7,0x28) return? hex(int((0xa1df-0x7)/float(0x76))+1+0x28) => 0x188
| |
assembly-3
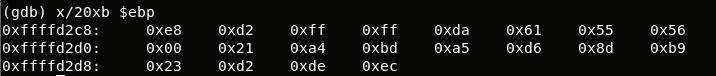
What does asm3(0xbda42100,0xb98dd6a5,0xecded223) return? 0x478
| |
有几点需要注意。一是数据采用小端序存储,高字节在高地址,[ebp+0x8]的值是0x00而非0xbd;二是 sub 0x00,0xa5 的值是0x100-0xa5=0x5b 。 三是WORD PTR [ebp+0x10] 的值是0xd223 而非0x23d2 。
可参考 此处 将汇编代码编译成共享库在C程序中调用。执行得到结果,也可调试加深理解。
| |
assembly-4
picoCTF{1_h0p3_y0u_c0mP1l3d_tH15_3242969916}